As we work to realize our vision for 2030 with an eye to future DX promotion, we are increasing the sophistication of our cybersecurity as a key part of our business infrastructure.
Basic Approach
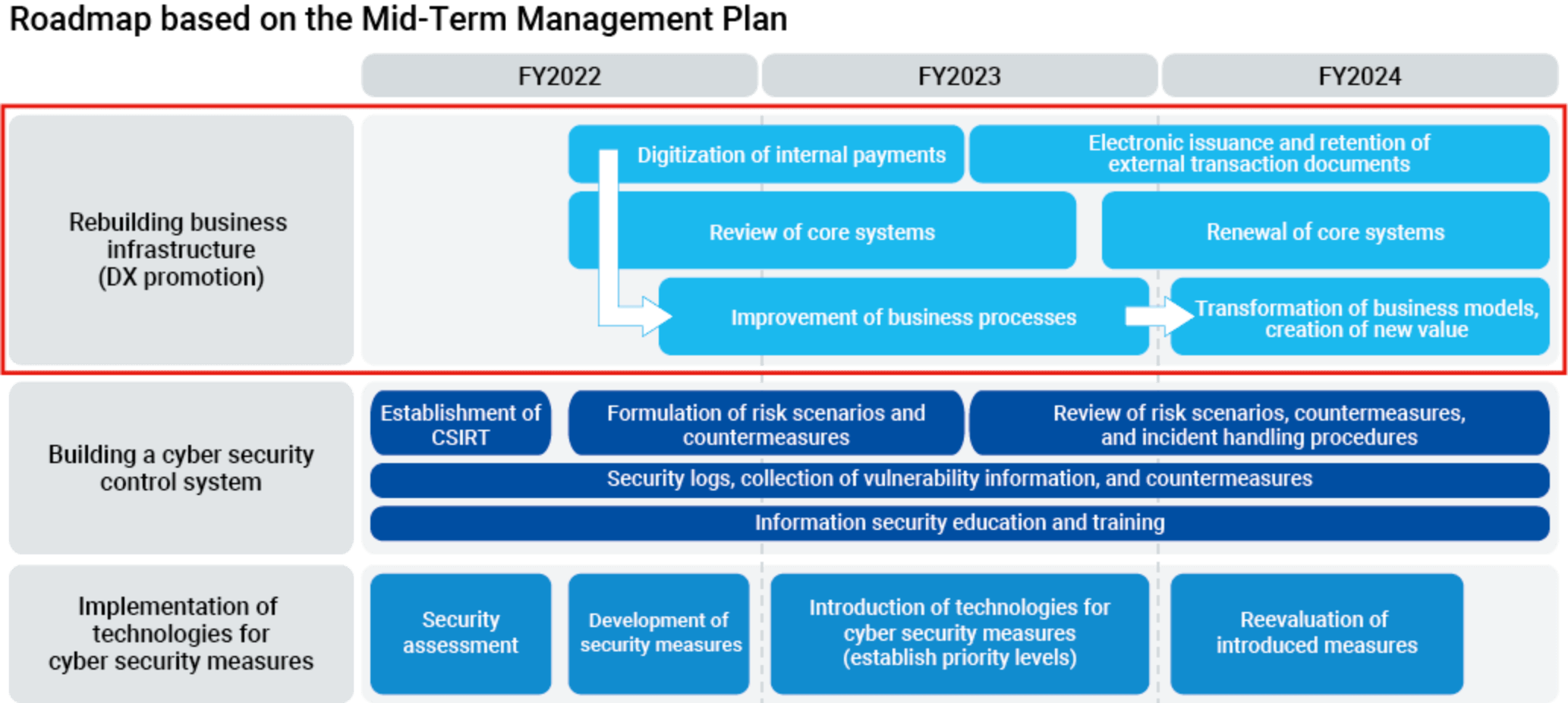
Cyberattacks are becoming more sophisticated and complex every year. In our corporate activities, we believe that it is extremely important to prepare for the threat of cyberattacks from the perspective of business continuity and the protection of personal information. Moreover, as the Group is responsible for supply chains in various industries, we need to implement cybersecurity measures across entire supply chains. As such, we are aiming to further strengthen the Group's cybersecurity approach to prepare for an increase in more sophisticated and complex cyberattacks as part of the "Rebuilding of business infrastructure" strategy set forth in the Mid-Term Management Plan, Challenge 2024.
Cybersecurity Management System
Establishing Computer Security Incident Response Team (CSIRT)
Carlit and Group companies have each established a CSIRT as an organizational structure dedicated to handling the Group's cybersecurity. These CSIRTs will implement Group-wide cybersecurity measures and respond promptly in the event of an incident.
Appointing Chief Information Security Officer (CISO)
We will appoint a CISO as the chief of cybersecurity officer for Group companies. The officer in charge of IT is to take on the role of CISO, and handle cybersecurity measures for the entire Group at the management level.

Specific Initiatives
We will carry out specific cybersecurity initiatives on both organizational and technical fronts to prepare for cyberattacks.
For organizational measures, we will establish a Group-wide security system. Moves on this front include establishing incident response procedures and sharing and handling security-related information, while also establishing CSIRTs at each Group company and coordinating with each CSIRT. We will also establish regulations and rules related to cybersecurity and offer security training as Group-wide initiatives.
As for technology to counter cyberattacks, we will introduce security technology at access points, internally, and at endpoints to protect information assets through a multi-layered defense.
When introducing these technologies, we will also work to standardize the level of security across the entire Group by aligning implementation policies with each Group company.
Roadmap for Mid-Term Management Plan, Challenge 2024